From attacks on mobile devices to ever-increasing types of malware, cybersecurity has never been more challenging. One of the best ways to stay protected is to be aware of cybersecurity threats. To that end, here are five common ways your IT systems can be broken into.
Here are some ransomware decryptor sites you should keep handy
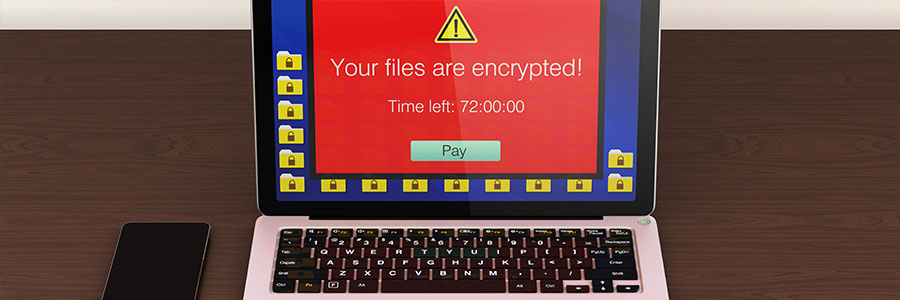
Ransomware is on the rise, but falling victim to one is not the end of the world. You can try some of these ransomware decryptors and maybe one of them will work. These are especially useful against automated “zombie” ransomware types.
The state of ransomware in 2021 so far
Businesses need to deal with ransomware both from outside and within.
What are security audits and why do you need them?
Make site visitors feel secure with these tips
Signs you have weak enterprise security

As cyberthreats become more sophisticated, many businesses need to prioritize cybersecurity more than ever. But are you sure that your security measures are keeping your enterprise IT assets safe? Here are five signs that they may not be effective.
Open wireless networks
With just one main internet line and a couple of wireless routers, an entire office can get online.
Don’t be a victim of juice jacking

Smartphones have become an indispensable tool for most of us. We use them for a wide range of activities, from gaming to checking social media to accessing work apps. Because of heavy use, our smartphones may sometimes run out of battery. When that happens and you’re out in public with no access to your charger, using public charging kiosks to bring your phone back to life can seem like a good idea — but it’s not.
Two excellent ways to verify user identity

A secure login process is an excellent way to protect your business from cybercriminals.
When it comes to verifying user identity, you can choose between two-step authentication and two-factor authentication. Learn the difference between the two so you can have a better appreciation of your cybersecurity options.
Why managed IT services is best for cybersecurity

Today’s companies need technology to function. Without it, businesses cannot compete and succeed. But with technology comes the ever-constant threat of hackers and cybercriminals. That’s why small- and mid-sized businesses need to protect themselves with robust cybersecurity solutions managed by IT professionals.
What does proactive cybersecurity entail?
Why using a VPN is more important than ever before

In the past, a simple antivirus software was all you needed to stay safe from online threats. Today, it takes more than that to protect your PC and the information stored on it. Whether you’re sending an important email or chatting with a coworker online, chances are your data can be easily intercepted.




